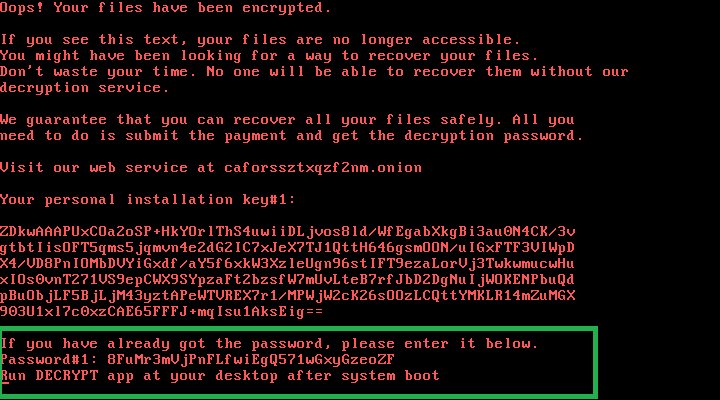
A major ransomware attack is hitting computers in Russia and Ukraine, bearing similarities to the NotPetya outbreak that caused billions of pounds of damage in June.
The self-titled “Bad Rabbit” malware encrypts data on infected machines before demanding a payment of 0.05 bitcoin (£250) for the decryption key. The ransom demand is phrased similarly to that of June’s outbreak, and researchers at Russian security firm Kaspersky say that the malware uses “methods similar to those used” during the NotPetya attack.
Among the affected organisations are Kiev’s metro system, Russian media organisation Interfax and Odessa airport. Interfax was forced to publish to its Facebook page during the outage, since its servers were taken offline for a number of hours.
Unusually, the malware’s code is peppered with pop culture references including the names of two dragons from Game of Thrones and the character Gray Worm used as names for scheduled tasks. A list of passwords that the malware tries while attempting to spread also includes “love”, “sex”, “god” and “secret”, which were dubbed the “four most common passwords” by the 1995 movie Hackers. In fact, the four most common passwords are 123456, 123456789, qwerty, and 12345678.

“Our observations suggest that this been a targeted attack against corporate networks,” Kaspersky’s researchers said, again suggesting a link between this outbreak and June’s. The NotPetya outbreak began through the release of a compromised version of a popular Ukrainian accounting program, spreading automatically throughout corporate networks.
The strongest link between the two attacks is based on the web servers which were used to distribute the initial software. Kaspersky researcher Costin Raiu told Forbes magazine that a network of hacked sites initially linked to NotPetya in July was now being used to host secondary distribution channels for Bad Rabbit.
But the two attacks contain a number of notable differences, as well. Where NotPetya was targeted at Ukraine, Bad Rabbit appears to have primarily hit Russian businesses. It was initially seeded through a fake Adobe Flash update placed on at least three hacked Russian media outlets, and from that initial foothold has spread through Russia and Ukraine, as well as other eastern European countries including Poland and Bulgaria.
The attack is also different from NotPetya in its mode of distribution. The fake Adobe Flash update which initially installs it doesn’t use any software exploits to run, instead relying on old-fashioned trickery to convince a user to open it themselves. Also, once installed, the software doesn’t use the famous EternalBlue exploit, believed to have been developed by the NSA before being stolen by a hacking group known as The Shadow Brokers, to spread within corporate networks. That decision may have limited the dispersal of the outbreak.
Perhaps the biggest difference between the two is that Bad Rabbit does not appear to be a “wiper”, as was suspected of NotPetya. That malware was basically impossible to remove, even for users who attempted to actually pay the ransom, leading to suspicions it had been created more to cause damage and destruction than raise revenue for its developers. Bad Rabbit, by contrast, reportedly does decrypt the hard drive upon entry of the correct password.
The UK’s National Cyber Security Centre said in a statement, “We are aware of a cyber incident affecting a number of countries around the world. The NCSC has not received any reports that the UK has been affected by this latest malware attack. We are monitoring the situation and working with our partners to better understand the threat.”
Carl Leonard, a principal analyst at Forcepoint, said: “We will continue to see massive attacks with economic, employee and public safety ramifications. And the methods will continue to evolve, including the evasive methods to hide their activity as well as their true intent.
“The trick will be to better understand the human points in these attacks. The intent or motivations of the attackers can range broadly including financial gain, revenge, political or hacktivism. Understanding these intentions can help shape our security strategies.”
Anton Ivanov
(@antonivanovm)Unlike #ExPetr, #BadRabbit is not a wiper. pic.twitter.com/JeBnD8q9DV
Initially, few security products were capable of stopping the outbreak: a sample of the malware uploaded to analysis service VirusTotal showed just four products correctly flagging it as malicious as of 4:30pm on Tuesday, including ones made by Kaspersky and Symantec. By then, the outbreak was well and truly underway. As of Wednesday morning, almost two thirds of updated security products correctly identify the malware.
Users without working antivirus protection can also reportedly protect themselves with a “vaccine” by creating a file on their computer before the malware does.
Amit Serper
(@0xAmit)Vaccination for the Ukraine round 2? Wanna stop #badrabbit?
Create a file called c:windowsinfpub.dat and remove all write permissions for it. This should keep the malware from encrypting. Testing it now… pic.twitter.com/3MSSH8WKPb


















![[Book Review] The Blade Itself (The First Law Trilogy) by Joe Abercrombie](https://bendthekneegot.com/wp-content/uploads/2018/01/1516047103_maxresdefault-218x150.jpg)